I never planned to work in cyber security!
But after tricking members of the White House, and what felt like the CEOs of most of the banks, my career as a web designer had come to a permanent end.
A recap of some of those I tricked as the ‘email prankster’:
CEO of Barclays Bank
Governor of the Bank of England
CEO of Citi Bank
CEO of Goldman Sachs
CEO of Morgan Stanley
CEO of Boeing
White House Chief of Staff
White House Counsel
Head of Homeland Security
US Ambassador to Russia
Eric Trump
UK Home Secretary
UK Shadow Home Secretary
(You can read more on the Social Engineering Wikipedia page and on my own Wikipedia page)
Tricking members of The White House into thinking I was a colleague of theirs got more media attention than I expected. And more attention from where I worked than I expected. Whoops.
…It even prompted the first ever mention of ‘spear phishing’ on US late night TV.
I think it caught the public’s attention because it’s something you assume won’t be possible to pull-off, especially against big banks, and the White House. Something would stop it, right?
Eventually my identity got out (I did nothing to cover my tracks other than not say my name tbf), and it was no longer about what I was ok with, I had to respect it was now affecting family and friends.
Retirement
So after a busy 5 month period known only as the ‘EMAIL PRANKSTER’, I hung up my keypad (I did 99% of the pranks on my iPhone) and hoped for the best.
Dec 2017. The EMAIL PRANKSTER™ chapter ends.
Now for the tricky part - Making my experiences count for something
I had a small window of opportunity to throw myself towards the security industry. I say window, it was more a grease-covered ledge, behind a cat-flap.
Don’t believe the trope that hackers just do a few high-fives, and the company limo swings in to pick you up, that only happens in films!
Hello Silicon Valley!
Well kinda, I was remote.
Introducing: James the Email Threat Researcher.
Thankfully, luck was on my side, and I landed a role in email security, working on some cool secret projects. Now I was socially engineering cyber criminals, not CEOs!
I learnt how BEC (Business Email Compromise) scammers profit from spear phishing and social engineering, and saw how technology and law enforcement work to try and control the ever-increasing damage these attacks cause.
Engagement with scammers targeting our customers was one one part of what we did, another was collecting data that went deep into their operations, to uncover what sat behind what can be a fairly innocuous looking ‘phish’.
At times it was shocking in a good way - like finding a scammer’s genuine passport. Other times it was shocking in an upsetting way - like seeing romance scam victims subjected to what can only be described as emotional abuse.
During my threat researcher days I was fortunate enough to work with the Secret Service, NCFTA, and FS-ISAC, providing them with actionable information to disrupt the scammers and their infrastructure.
I am proud I got the opportunity to make a difference, and realise it probably didn’t change that much. But I met lots of people who cared, and the small things add up.
But it changed me, seeing how wild cybercrime is, and I wanted to at least try and help people to be safer, and that’s all that drives me today. To do my best to make scammers less successful against us.
June 2020. I started focussing on my own projects.
It’s been great to soak up a new side of the industry - security training. And can’t believe how much there is to explore.
A risk for everyone
The power of social engineering is it doesn’t get less effective the more intelligent the target is.
I looked back at the education of those I tricked during my prankster days, and the majority had law degrees, one even had a Masters in Aeronautics and Astronautics - an actual rocket scientist.
So we can’t rely on just our wits and spider-senses to keep us safe. There is a real need to understand the nature of these attacks, or the scammers will have the upper hand.
Recap on how often i’ve ended up in a CEO fraud vortex:
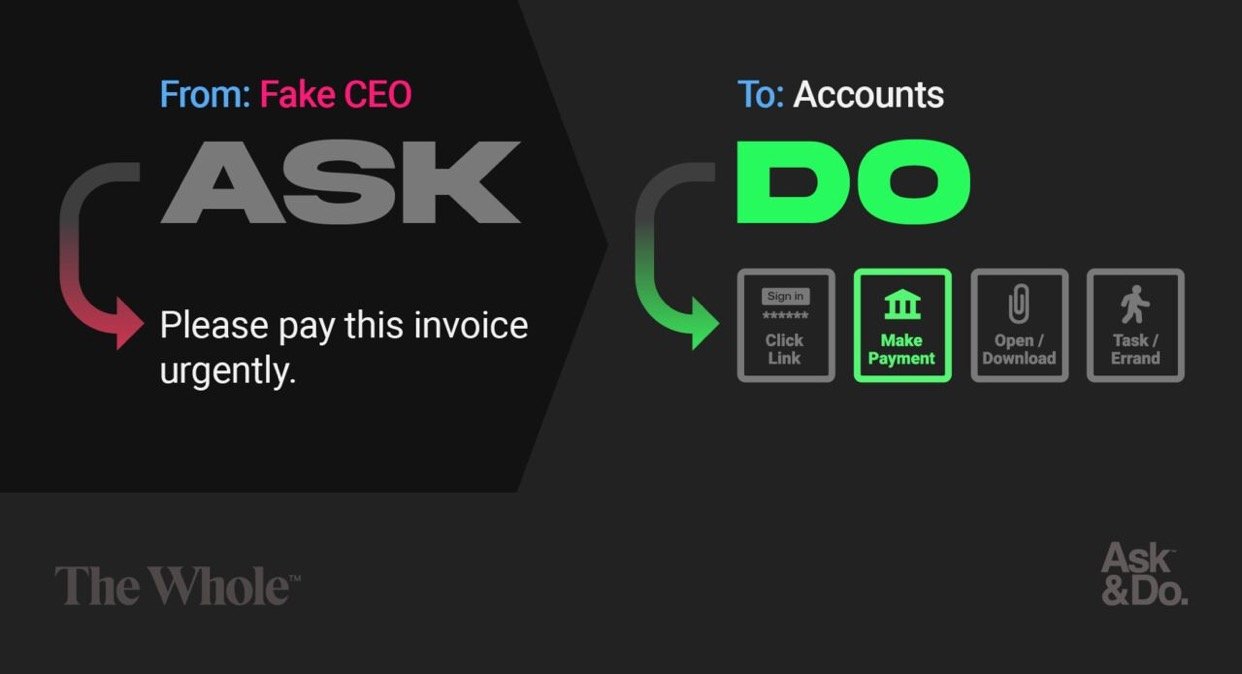
I pretended to be my CEO to trick colleagues (over email)
I then pretended to be a chairman to trick CEOs (over email)
Then I tricked cyber criminals, who pretended to be CEOs (over email)
Now I teach employees how to not be tricked by cyber criminals pretending to be CEOs (over email)
The truth is facinating enough
I’m a big believer that the truth about the risks we face is one of the most powerful educational tools we have. Everyone already cares as much as they feel they need to, and they won’t be open to revise those beliefs unless they genuinely buy into the problem on a more personal level.
Which is why I never tire of talking about my own personal story — it’s the the best way for me to help people to be safer.
Please feel free to head over to my personal Linkedin profile, if you’d rather DM me directly on there.